Aside from the poor Radiohead reference , really, please quit with the spam. As I’m sitting in earnest trying to learn more about assembly language before returning to university, I have been peppered with spam.
Spam is much more interesting than an informative 1464 page PDF Assembly text.
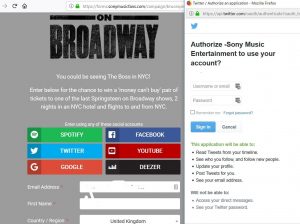
This was one of the more poorly crafted Spam mails I’ve seen – the sender address is definitely not Paypal. So why bother look further?
Curiosity or procrastination is the answer, I’ll let you decide.
So, I thought I’d fire the spam at a free online sandbox in the interests of practical application of what I am about to study. The sandbox ultimately does some of the hard work and since I dont fully understand reverse engineering yet, I’ll let the tools do the heavy lifting. (I’m still trying to learn remember?)
The domain connected to the login scam was registered today – usually a good sign of something interesting
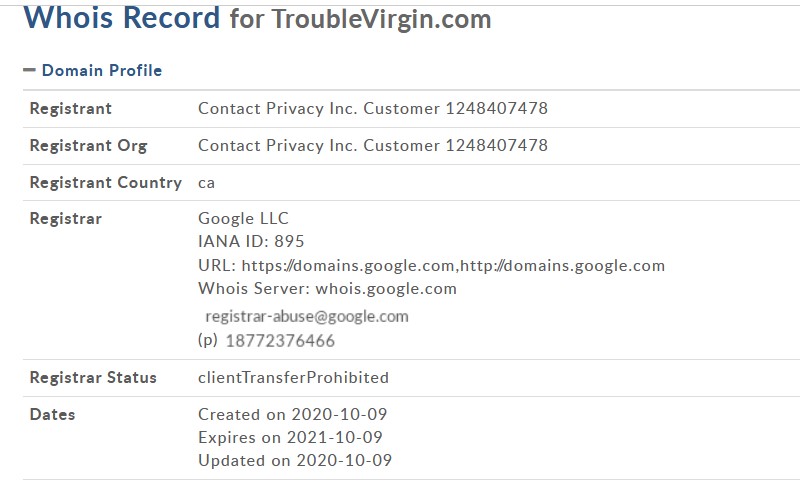
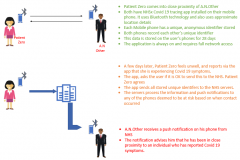
When one of the sandbox analysis execution had completed, I got some more good info. The paylod will attempt “API Hooking”. Effectively this is where a malicious process will attempt to “hook” into a system API call. This time the intention was most likely to grab user credentials from the PayPal “login”
FYI – There is a great book on Windows API calls that is also part of my course pre-reading. It’s very accessible and worth a read.
You can also read more about this attack technique in simple terms from the good people over at Mitre.
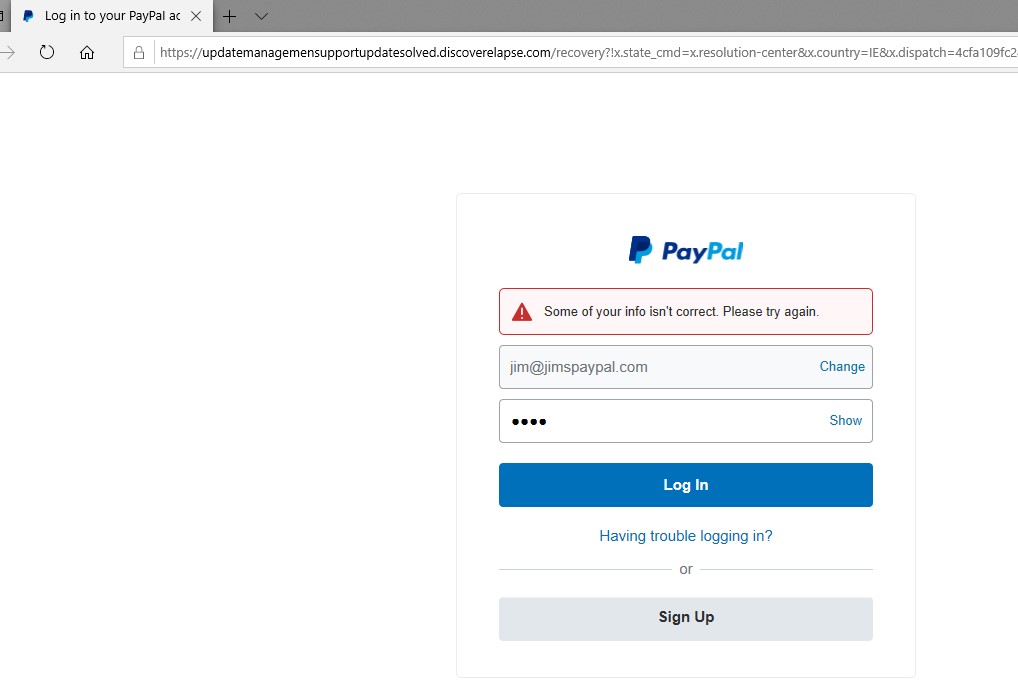
Another aspect of the sandbox analysis is that it has uncovered the potential Command & Control server. This is where the malware “phones home” and awaits instruction/sends data. Once again my curiosity got the better of me, so I’ve turned on a sandboxed PC to try the link. It didn’t disappoint – a great fake Paypal Login page. (aside from the URL)
The sandbox also outlined that there was manipulation of the Trusted Root certificate store, which might enable the malicious site to fool the user as there may be no “invalid certificate” browser warning. I haven’t had time to really investigate this certificate further. If you’re interested in reading why this might be an issue there is some more great content via Mitre.
The danger of using a “free” sandbox is that the output is shared and so within an hour of me starting the “investigation” it seems like the specific link has been shutdown.
The IP addresses uncovered have a poor history:
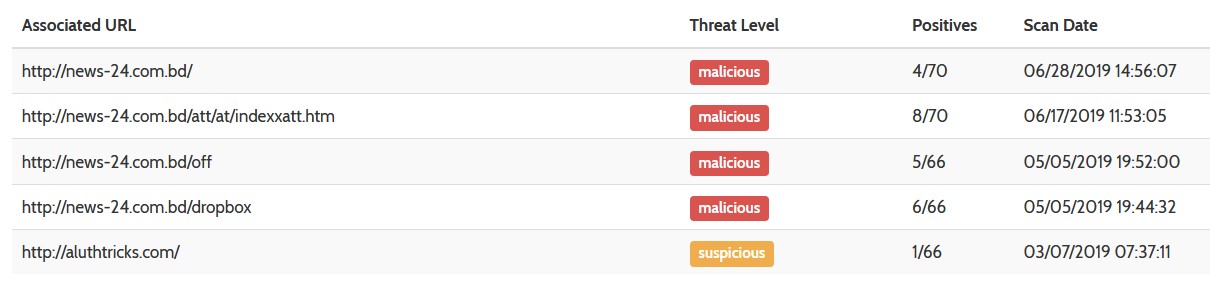
It’s likely there will already be another domain registration associated to this IP addresses and some other lucky people wil be bombarded with SPAM.
Now that I’ve got this out of the way it’s time to mov eax, ebx and get on with the studying!