What is contact tracing?
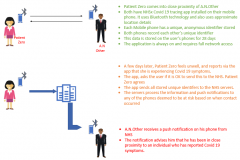
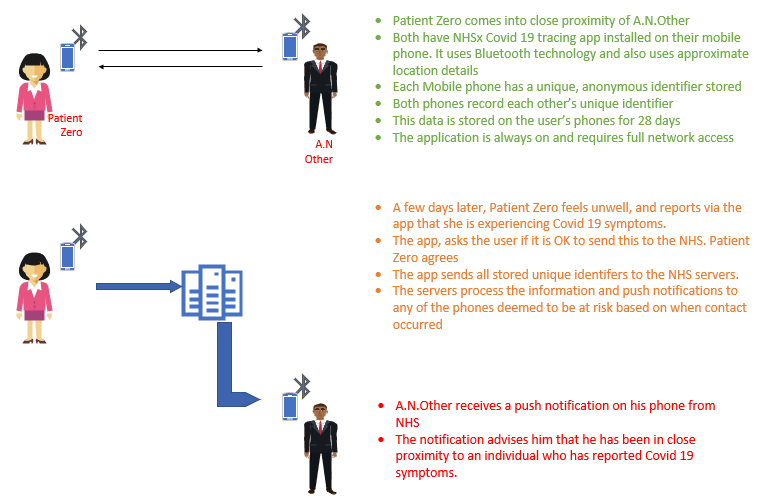
Contact tracing is a process where an individual voluntarily installs an application onto their mobile device. The application is designed to use the functions of the mobile such as Bluetooth and networking capability. The application aims to create a record of other devices which have been in proximity. The operation of the application is explained further in Figure 1 below.
There are two main contact tracing scenarios, centralised and decentralised. NHSx has designed and published an application based on the centralised approach[1]. The focus of this assignment is on the centralised model.
Centralised Approach
The original diagram below outlines how the Centralised approach to tracing works. It summarises the information presented by NHSx.[2]
Figure 1 – Centralised Contact Tracing
Relevant Laws
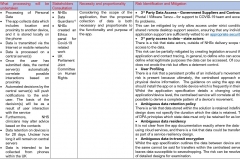
There are several laws with which the application needs to comply.
|
Law
|
Why this is important
|
|
General Data Protection Regulations (GDPR) EU 2016/679
|
“GDPR sets out key principles, rights, and obligations for processing personal data”[3]. It is a European regulation which has been implemented in each member state. It remains in force for as long as Britain remains a member of the European Union and it will be written into the Withdrawal Agreement. There are some subtle differences between GDPR and DPA. However, it is the basis of the revised DPA 2018.
Personal data is information which relates to an individual or identifiable individual[4]. The data collected by the app is pseudonymised. However, there are sufficient constants within the data that may enable a technically skilled actor to seek out an individual effectively. The NHSx Data Privacy Impact Assessment highlights the rationale for declaring why it considers the data to be personal. This document is in “Approved” state.
|
|
Data Protection Act 2018 (DPA)
|
DPA 2018 is the UK government implementation of the GDPR. It is read in conjunction with GDPR. The fundamental reason for DPA applying to this application is that it is collecting information about individuals.
NHS is defined as a Data Controller under DPA. The DPA governs how any organisation must act with regards to their approach to obtaining and processing data.
There are several Data Protection Principles within the act, listed below. The NHSx App must comply with these.
· Lawfulness, fairness and transparency
· Purpose limitation
· Data minimisation
· Accuracy
· Storage limitation
· Integrity and confidentiality
· Accountability
|
|
European Human Rights Law
|
Article 8 – Right to respect for private and family life, home and correspondence. Users who have agreed to install the app expect privacy namely that any data harvested from the phone within the app will not be used for purposes other than tracking the spread of Covid-19 and advising whether there has been any contact with potentially infected individuals.
|
|
Health and Social Care Act 2012
|
The HASCA required the establishment of the Health and Social Care Information Centre. This later became known as NHSx or NHS Digital[5]. Within this act, NHS Digital is required to comply with the Code of Practice on Confidential Information[6] outlined in Section 263 (1-7) This is summarised as the Coldicott principles[7].
|
|
Freedom of Information Act 2000 (FOIA)
|
The FOIA sets out how Public authorities must publish certain information about their activities and grants member of the public access to information held by public authorities in Great Britain and Northern Ireland. In the context of Covid 19 application, NHSx has already, proactively, published substantial details on the application[8] . There will likely be future FOIA requests to release more detailed data.
|
|
Control of Patient Information 2002 (COPI)
|
These regulations set out the conditions under which confidential patient data may be shared within the healthcare setting. Although the app itself will not share personal indicators such as name, address and date of birth, there is a requirement to adhere to COPI. Specifically, regulation 3 provides for the processing of confidential patient information for purposes relating to infectious disease and other risks to public health. The current thinking from NHSx is that “We are working on the basis that information about health symptoms that users report using the App may qualify”[9]
|
Data Privacy Impact Assessment
Since the introduction of GDPR and DPA 2018, PIA is now known as Data Privacy Impact Assessment. The DPIA structure has been obtained from ICO[10]
Conclusion
There are several issues with the application and the presentation of related information:
- The absence of specific legislation supporting how the application is governed. While existing legislation such as DPA and GDPR provide elements of governance and control around data, they do not necessarily align with Article 8 from the European Convention on Human Rights. There is a valid counterargument that application usage is voluntary, and users of the app are asked to consent to share data. However, it is beyond a reasonable expectation that most users of the application will fully understand the broader ramifications of the application data and the issues outlined in the DPIA above.
- The decision to build a centralised application contravenes a recommendation of the Information Commissioner’s Office[13]. It also represents a conflicting approach in respect of major smartphone manufacturers who have opted to develop a decentralised model[14].
- The right to be forgotten. While users can uninstall the application from their phone, and this removes data from the device, it is unclear whether that action removes server-side data. However, it should also be noted that as this application has been developed for public health reasons, it is unlikely that this applies.[15] The right to be forgotten is not an absolute right.
- Application design is ambiguous. When reviewing the design document,[16] there is a reference to “other systems” these are undeclared at the time of writing. Risk is therefore introduced as to what these systems are, where they reside, what data is being transferred and who might have access to the data.
- Due to how an application user can submit that they are experiencing symptoms of Covid-19, it is possible that malicious individuals could falsely report. Further to this, it would also be possible for a malicious individual to carry out an amplification attack whereby the number of contacts could be deliberately increased. This amplification could force NHS into deploying resources where they are not needed. A similar incident has happened recently in Berlin[17].
- As a result of the previous point, there is also a potential impact on otherwise healthy individuals as they may receive a ‘false-positive’ notification that they have been in contact with a suspected Covid-19 positive individual. Because the decision making on the central servers is effectively automatic many individuals could be wrongly advised on their potential Covid-19 status.
- There are numerous contradictory statements concerning the nature and classification of data. Matthew Gould, CEO NHSx[18] and Ian Levy[19] have said in independent reports that the application does not hold or generate any data which would be considered personal. However, this contradicts the NHSx DPIA for the application9
[1] https://covid19.nhs.uk/
[2] https://covid19.nhs.uk/how-the-app-works.html
[3] https://ico.org.uk/for-organisations/guide-to-data-protection/introduction-to-data-protection/about-the-dpa-2018/
[4] https://ico.org.uk/for-organisations/guide-to-data-protection/guide-to-the-general-data-protection-regulation-gdpr/key-definitions/what-is-personal-data/
[5] https://www.gov.uk/government/news/hscic-changing-its-name-to-nhs-digital
[6] http://www.legislation.gov.uk/ukpga/2012/7/part/9/chapter/2/enacted
[7] https://digital.nhs.uk/data-and-information/looking-after-information/data-security-and-information-governance/codes-of-practice-for-handling-information-in-health-and-care/code-of-practice-on-confidential-information
[8] https://github.com/nhsx/COVID-19-app-Documentation-BETA
[9] Data Protection Impact Assessment NHS COVID-19 App PILOT LIVE RELEASE Isle of Wight
[10] https://ico.org.uk/media/for-organisations/documents/2553993/dpia-template.docx
[11] It is not clear from the application documentation that possibility of location leakage has been contained. https://developer.android.com/guide/topics/connectivity/bluetooth#Permissions
[12] https://www.gov.uk/government/organisations/national-data-guardian
[13]https://ico.org.uk/global/data-protection-and-coronavirus-information-hub/blog-combatting-covid-19-through-data-some-considerations-for-privacy/
[14]https://ico.org.uk/global/data-protection-and-coronavirus-information-hub/blog-combatting-covid-19-through-data-some-considerations-for-privacy/
[15]https://ico.org.uk/for-organisations/guide-to-data-protection/guide-to-the-general-data-protection-regulation-gdpr/individual-rights/right-to-erasure/
[16]https://github.com/nhsx/COVID-19-app-Documentation-BETA/blob/master/Overview%20-%20External%20system%20linking%20with%20Privacy.pdf
[17]https://www.theguardian.com/technology/2020/feb/03/berlin-artist-uses-99-phones-trick-google-maps-traffic-jam-alert
[18] Q20 – https://committees.parliament.uk/oralevidence/334/pdf/
[19] https://www.ncsc.gov.uk/blog-post/security-behind-nhs-contact-tracing-app